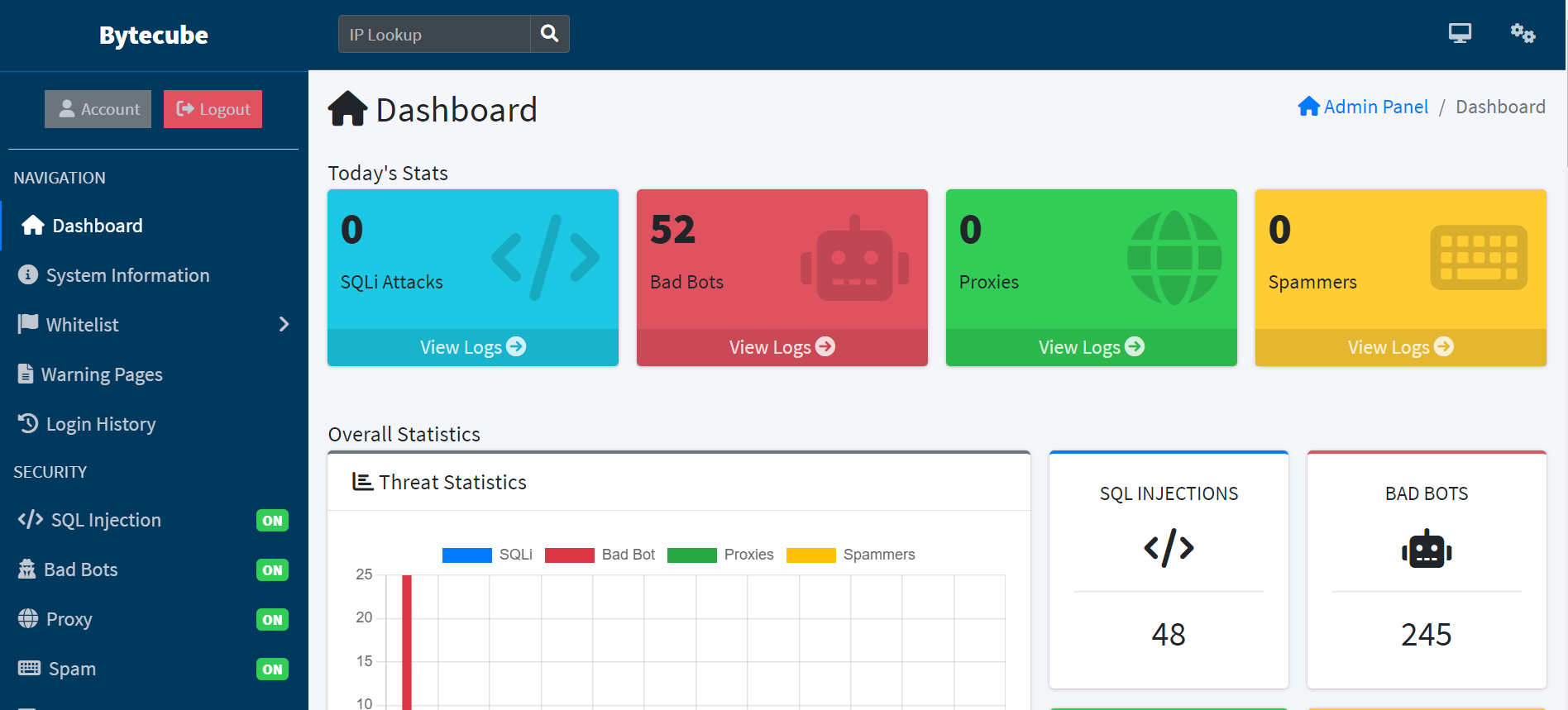
It comes with powerful admin panel from which you can view all logs and it is also integrated with Ban System from which can be banned Visitors (IP Addresses), Countries, IP Ranges, Internet Service Providers (ISP), Browsers, Operating Systems (OS) and Referrers. The Admin Panel has many features and settings. Through it can be easily managed the security of your website.
Bytecubeis a powerful Web Application Firewall designed to protect all PHP softwares, from custom scripts to popular shopping cart softwares and CMS applications. It allows any website administrator to benefit from very advanced and powerful security features. It is very fast, optimized and requires very low system resources.
PROTECTION MODULES
Protect your Web Application from SQL Injections (SQLI), XSS Vulnerabilities, Spammers, Bad Bots, Proxies, VPNS, TOR Visitors and many other threats. Depending up on the usage you can enable or disable the features under protection module.
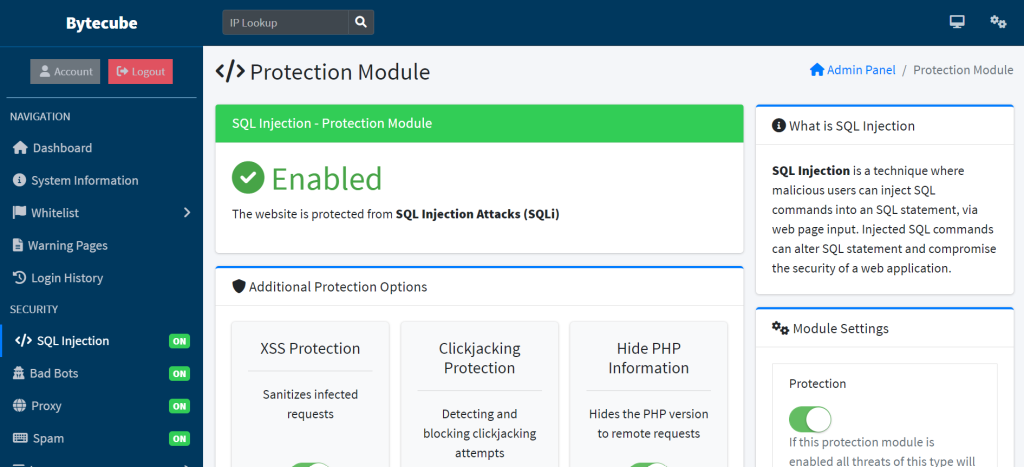
Protection modules is a system designed to protect servers or systems from damage or malfunction. They can be used in a wide range of applications, and computer networks.Protection modules is used in software systems to protect against unauthorized access or malicious attacks.
THREAT LOGS
Threat logs are a type of security log that capture information about potential security threats to a system or network. They can be used to track events such as attempted unauthorized access, suspicious network activity, and other security-related incidents. This information can be used to identify and investigate potential security breaches, and to develop strategies for preventing future incidents.
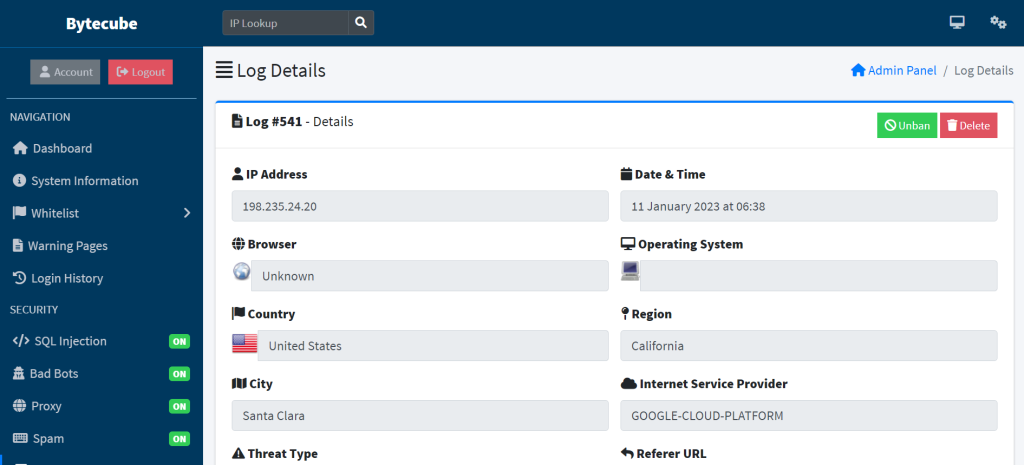
In security applications, threat logs are typically generated by security devices such as firewalls, intrusion detection and prevention systems, and security information and event management (SIEM) systems. These logs contain information about the source and destination of network traffic, the type of activity that occurred, and other details about the event. This information can be analyzed to identify patterns of suspicious behavior and to identify potential security threats.
Threat logs can also be integrated with other types of logs, such as system logs and application logs, to provide a more complete picture of activity on a system or network. This can be useful in investigating a security incident, and also to trace back the origin of the attack.
It is also important to securely store and protect the logs as the logs contains vital data that can be used by attacker to track back their activities to compromise the system again.
BAN SYSTEM
Ban system in bytecube is a feature found in security applications, such as firewalls, intrusion detection and prevention systems, and other network security devices, that allows administrators to block or restrict access to a specific IP address or network. This is typically done in response to a detected security threat, such as a hacker attempting to gain unauthorized access to a system, or to block malicious traffic, like a botnet command and control server.
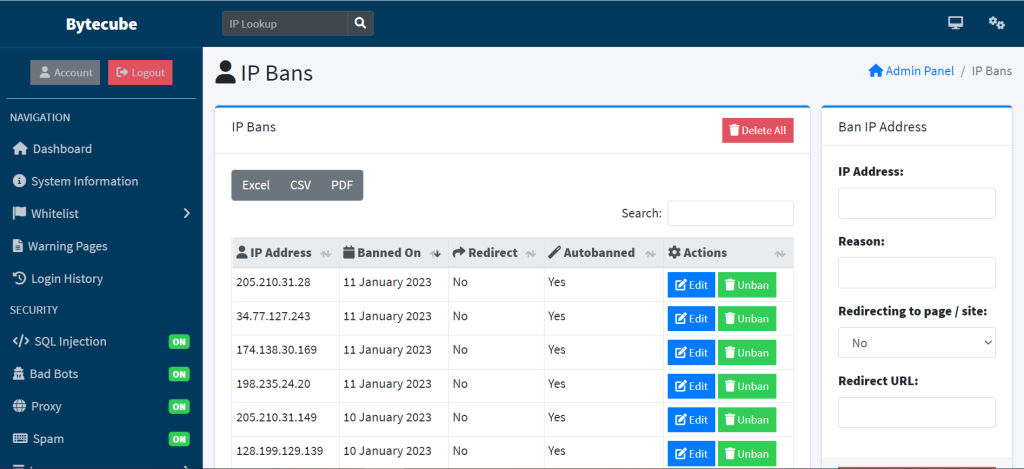
In Bytecube, an administrator can configure the system to automatically block access to an IP address or network when certain conditions are met. For example in bytecube, an intrusion detection system will be configured to automatically ban an IP address if it detects a specified number of failed login attempts from that address.
In this ban system an administrator can also include a manual process, where the administrator have the ability to add and remove the IP addresses to be blocked. This is beneficial in cases where a false positive or someone who has access to a blocked IP address needs to be unblocked.
It’s worth noting that a ban system does not guarantee total security on the network or application, as a determined attacker may use a different IP address or find another way to gain access to the system. However, it can be an effective tool for reducing the likelihood of successful attacks and for limiting the impact of security breaches.
SYSTEM INFORMATION
System Information in bytecube is included with information about the system or network being protected, as well as information about the security threats and incidents that have occurred.
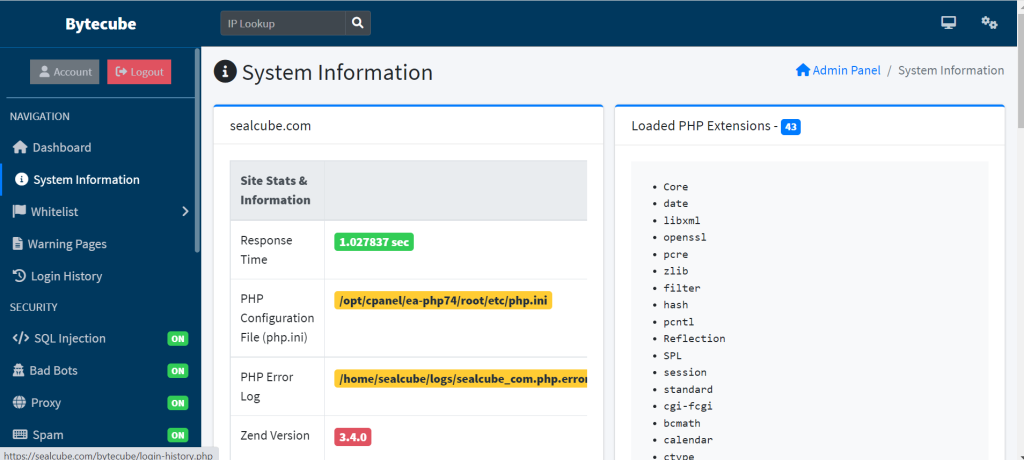
In security applications, system information can be used to gain insight into the current state of the system or network, to detect and respond to security threats, and to track the effectiveness of security measures. Examples of the types of system information that may be collected include:
- Configuration information: This can include details about the hardware and software that make up the system or network, as well as information about the specific security settings and policies that have been configured.
- Activity logs: These can include system logs, application logs, and security logs that provide information about events that have occurred on the system or network, such as login attempts, file access, and network traffic.
- Performance metrics: This includes metrics such as system resource usage, network bandwidth, and response time that can be used to monitor the overall health and performance of the system or network.
- Threat Intelligence: This includes data related to known threat actors, vulnerabilities, malware and botnet campaigns, phishing attempts and more that can be used to improve the security posture of the system or network.
It’s important to note that System information is also used to evaluate the security posture of the system and to create more effective security policies and procedures to prevent future attacks.
FEATURES
Bytecube security application is featured with firewalls, intrusion detection and prevention systems, and antivirus software, typically include a variety of features designed to protect a system or network from security threats. Some of the features found in bytecube security application include:
Protection from Spammers and Spam Bots that aim to spam your website.
Protection Module that automatically sanitizes all incoming and outgoing requests and responses. Real-time scanning of all requests.
Protection module that filters profanity, bad words, bad links, bad sentences and other bad content in real-time.
Integration with some of the best Spam Databases (DNSBL) to protect your website from Bad Visitors.
Detects Unknown and Zero-Day Attacks and Exploits.
Tool that help you investigate IP Address and check if it is blacklisted.
You will receive an E-Mail Notifications when attack or threat is detected.
On the Dashboard you can check the Stats for the protection of your website.
Collection of Tools such as .htaccess Editor, Hash Generator and other.
Useful tool that shows all logged errors from your website.
Edit your .htaccess file directly from the Admin Panel, no need to open it in any external editor.
A list of IP Addresses and Files that will be ignored by the app and will not be blocked.
Observe your visitors in real time as they interact with your website.
Block and redirect Visitors / Users (IP Addresses), Countries, IP Ranges, Operating Systems, Browsers, Internet Service Providers (ISP) and Referrers.
Protection from Proxy, VPN and TOR Visitors or so-called people hiding behind proxies.
Verifying search engine bots that visit your website whether they are real or fake bots.
Every visitor’s response headers will be checked and if there are suspicious objects their access to the website will be denied.
Function that will automatically ban attackers and threats when bad behavior is detected.
Each threat and attack is logged into the database, so you can view them later. (No duplicates)
Tool that help you investigate IP Address and check if it is blacklisted.
The logs contain many information about the Threat / Attack like Browser, Operating System, Country, State, City, User Agent, Location and other useful information.
Track and analyze how people use your website.
Check current PHP Configuration for potential security flaws.
Page with a big amount of information and statistics about your web host.
The script is very lightweight and won’t slow down your website loading time.
Looks good on many devices and screen resolutions.
The script is integrated with Installation Wizard that will help you to install the app.